There are some requirements before you can get started.
- Licenses - you should consult the official docs but I have Microsoft 365 E3 for testing.
- Obviously we need an Azure subscription - this will cost you money (but not too much).
- User accounts - you'll need to nominate a WVD Tenant Creator and some test host pool users.
- You need to decide what directory services you will use to support your infrastructure. You can use Azure AD, DC hosted in Azure or a DC hosted on premises with a VPN to Azure. The Azure VMs that you create can be AD-joined or hybrid AD-joined (not Azure AD-joined.
- Azure network - you need to have a virtual network in Azure. Remember you don't configure DHCP in Azure virtual networks. IP addressing is dynamic based on the assigned subnet.
- I'm using a DC hosted in Azure so I configured a static DNS record for the DC in the properties of the virtual network. This way my VMs will be able to join the domain.
- Download and install the Windows Virtual Desktop PowerShell module. Launch PowerShell as administrator and run:
Install-Module -Name Microsoft.RDInfra.RDPowerShell
Import-Module -Name Microsoft.RDInfra.RDPowerShell
Setting up Windows Virtual Desktop
Now let's get started setting up the environment. The first thing we need to do is to allow Windows Virtual Desktop services to access the Azure AD tenant. For this we'll need the tenant ID (also referred to as Directory ID).
We can get the Directory ID in the properties of Azure Active Directory. Copy it be clicking on the blue box to the right. You'll need this a couple of times during this process.
Now navigate to
https://rdweb.wvd.microsoft.com (this is Windows Virtual Desktop services). Add your tenant ID and click
Submit for the Server App.
Accept that you are granting permissions to WVD.
This was successful.
Repeat the process for the client app.
Accept the permissions.
Enjoy the success. Now that we've granted access to Azure AD we need to grant permissions to a user to create a Windows Virtual Desktop tenant. Essentially we'll assign the "TenantCreator" role to a user account.
We do this in the Azure Portal.
Navigate to
Azure Active Directory and select
Enterprise Applications.
Select
Windows Virtual Desktop and choose
Users and Groups.
Select Add User and add the lucky user who will create the WVD tenant. I've chosen Fred. See that he is now a TenantCreator.
Now we'll create the WVD tenant. Remember we copied the tenant ID earlier (aka Directory ID). We're going to need it again. We'll also need the Azure Subscription ID.
It's easy to find. Navigate to your
Subscriptions using the search.
You'll find the subscription ID. Now's let's create the WVD tenant. We do that using PoSH. Sign in to Windows Virtual Desktop by using the TenantCreator user account with this cmdlet:
Add-RdsAccount -DeploymentUrl "https://rdbroker.wvd.microsoft.com"
Create a new Windows Virtual Desktop tenant associated with the Azure Active Directory tenant (you'll choose a tenant name and replace the bracketed values with your tenant ID and subscription ID):
New-RdsTenant -Name <TenantName> -AadTenantId <DirectoryID> -AzureSubscriptionId <SubscriptionID>
The WVD tenant has been created. Now we'll deploy a host pool of virtual desktops. Sign into the Azure Portal and select
Create a Resource.
Search for
Windows Virtual Desktop and select
Windows Virtual Desktop - Provision a host pool.
Choose to
Create a host pool. There are four pages of details to configure.
The first page has some basics.
- Choose the subscription that you want to use (there will be a cost).
- Select a Resource Group. It needs to be empty so you'll probably create a new one here.
- Select your region.
- Enter a name for the host pool.
- Choose the desktop type. Personal is where every user has a dedicated VM. I've chosen pooled.
- Configure the users that will log into these VMs (comma-separated list). Note that you'll also need to enter the TenantCreator here if he will need access. It is not automatic.
The next page is for our expected usage. This determines how many VMs will be deployed. Click
Change Size if you want to change any VM details. I'm conscious of cost in my lab so I've done that. Also enter a prefix for the names of the VMs
The third page allows you to configure the VMs. Choose the following:
- Image Operating System - I've chosen Windows 10 Enterprise multi-session with Office 365 ProPlus.
- Disk type - I've chosen Premium SSDs for performance.
- Domain join account and password - the account must already be configured on the domain. This requires password complexity so be careful here.
- Domain and domain OU - remember the VMs must be able to find the DC
- Virtual network and subnet - make sure your DNS configuration is in place.
The final page asks for the WVD tenant details. Enter the tenant name and the owner account details. That's Fred, who created the tenant.
Finally you're asked to review your configuration and then
Create the host pool.
The deployment is underway. You can see the detailed steps.
The deployment has completed.
The VMs have been created......
…..and joined to the domain.
Working with Windows Virtual Desktop
There are two ways to access the WVD pool from a desktop.
- Remote Desktop client
- Browser (HTML5 client)
I'm going with the full client option. You can download from
here
It's an MSI installer so just run and install as normal.
On the first launch you have to
Subscribe to WVD.
Sign in as a permitted user.
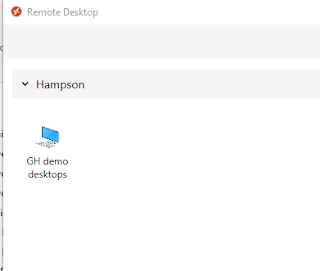
Looks like we're in business.
I can see my WVD host pool......
….and I've signed into one of my VMs.