(First published in Dec 2018 but I was too early so I withdrew the post 😃)
This has been one of the most requested Intune features for quite some time and, yesterday, it was released as a public preview in Intune 1901. What is it all about? You can find the official documentation here
For many years now we have relied on Microsoft to provide guidance on the security settings that we should configure. In the on-premise Active Directory world we don't want to analyse every possible GPO that is available. That's why we implement the Microsoft security baselines as a starting point and then we change individual settings as required. Microsoft have now provided Windows 10 security baselines for the Intune MDM-managed world. I tested it today and it's really easy to implement. It works well too.
Remember that this is a public preview only and is only supported with Windows 10 version 1809 and later. It is not yet recommended for production.
So where do we start? In the Azure portal, navigate to All Services and search for Intune. Select Security Baselines (Preview).
Launch Security Baselines and we can see the Preview: MDM Security Baseline for October 2018 (beta).
Drill into the baseline. Click Create profile.
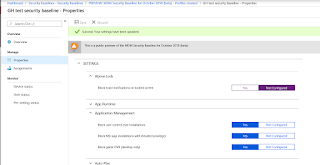
Enter some details (Name and Description) for your baseline (profile). The platform and baseline drop-down arrows are grayed out. These will probably become available as more baselines are released for different Windows 10 versions.
Have a look at the Settings. These are the kind of security heading that you would expect.
"Block toast notifications on locked screen" is enabled in the baseline. I'll check for that in my test computer in a minute.
The Browser settings look secure.....
....and these are the Device Lock settings. See that we will prevent the reuse of the previous 24 passwords. That's pretty secure. I'll check that on my test client also.
Once the profile has been created it should be assigned to a group (of devices or users).
Ok, on my test device, I've initiated a manual sync. Otherwise I'd have to wait up to 8 hours.
I've generated an MDM Diagnostics report.
These are the results. I can see that DevicePasswordHistory is now configured for 24.
AllowToasts is now disabled.
So what happens if I make a change to a baseline? Let's change the toast notification setting to Not Configured.
After a manual sync I can see that this setting is no longer managed.
I can see a lot of potential with this feature. Try it out (although not in production yet).
Until next time......














No comments:
Post a Comment