I was working with a new customer recently and they pointed out that they were having a problem with NDES.
What is NDES? The Network Device Enrollment Service (NDES) is one of the role services of Active Directory Certificate Services (AD CS). NDES acts as a Registration Authority to enable devices running without domain credentials to get certificates from the internal Certificate Authority, based on the Simple Certificate Enrollment Protocol (SCEP).
Therefore the customer was unable to issue SCEP certificates via Intune and was unable to enforce 802.1x authentication to their network.
An Intune managed Windows 10/11 client was a good place to start, in particular the event logs (Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider > Admin). Event IDs 307 and 32 were repeating.
Event ID 307 - SCEP: FailedLogError Message : (SCEPInstallCertificateWithScepHelper:Failed to Initialize SCEP enrollment with NDES Server https://xxxxx.msappproxy.net/certsrv/mscep/mscep.dll/pkiclient , CA Cert thumbprint 'xxxx' and server certs)
Event ID 32 - SCEP: Certificate enroll failed. Result: (Internal server error (500)).
Just for kicks I opened a browser and navigated to the NDES server URL (from event ID 307). It gave me the same Internal Server Error (500) that I could see in event ID 32.
Next I had a look on the NDES server. The IIS log files can be found in the following folder: %SystemDrive%\inetpub\logs\logfiles\w3svc1. On 10th August we could see a status code of 200: This status indicates the connection with the NDES server is successful.
On 11th August we could see a status code of 500. This Microsoft troubleshooting guide tells me that Status code of 500 could mean that the IIS_IUSRS group might lack correct permissions (Impersonate a client after authentication).
However, I opened the Local Security Policy editor (secpol.exe), expanded Local Policies, and then selected User Rights Assignment. Double-clicking Impersonate a client after authentication in the right pane, I could see that the IIS_IUSRS group had the correct permissions.
The SCEP application pool was started so no problem there.
The Application event log on the server gave me some direction. Event IDs 10 and 2 were repeating.
Event ID 10: The Network Device Enrollment Service cannot retrieve one of its required certificates (0x80070057). The parameter is incorrect.
Event ID 2: The Network Device Enrollment Service cannot be started (0x80070057). The parameter is incorrect.
This prompted me to look at the computer certificates on the NDES server. Sure enough, they had expired. There were three certificates to deal with: - Certificate based on the CEP Encryption certificate template
- Certificate based on the Exchange Enrollment Agent (Offline Request) certificate template
- Certificate based on the NDES SSL certificate template
Perfect, I just need to renew these certificates, right? Well not really.
I started with the CEP Encryption certificate, right-clicked on the certificate and selected
Request Certificate with New Key.
However the CEP Encryption template was not available so I couldn't "renew" the certificate. I needed a brand new certificate with exactly the same details.
I made a note of the Subject details for the existing certificate.
Now to create the new certificate, I right-clicked on the Personal folder and selected All Tasks > Request New Certificate.
I selected the Active Directory Enrollment Policy and clicked Next.
This time the CEP Encryption template was available. However more information was required. I clicked on the link to configure the certificate.
I added the same Subject details that I had captured earlier from the existing certificate, applied this and completed the wizard to generate the certificate.
The certificate was created with excessive permissions for the service account. I clicked Manage Private Keys.....
.... and unchecked the box for Full Control for the service account.
Next up is the NDES SSL Certificate.
It's the same process as above except this time we use a different template. Don't forget to remove the Full Control permissions from the service account when you are finished.
Last but not least we get to the certificate based on the Exchange Enrollment Agent (Offline Request) certificate template. The process to generate this certificate is a little different than the others. Nickolaj Andersen has published the steps in a good post
here. Please follow these steps to generate the third certificate. They are pretty straightforward.
I executed an IIS reset and figured that I was good to go.
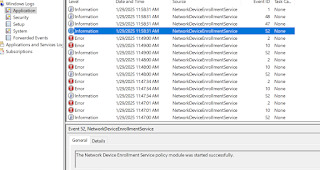
The Network Device Enrollment Service policy module started successfully.
NDES looked to be functioning correctly.
Happy days, the NDES service finally started. But alas, certificates were still not being issued. There were still errors in the clients event log referring to "BadGateway: This corporate app can't be accessed".
Opening a browser and navigating to the NDES URL gave the same information but also showed that the source of this error was the Azure AD Application Proxy. From that I figured that there was a communication error between the AAD Application proxy and the NDES server.
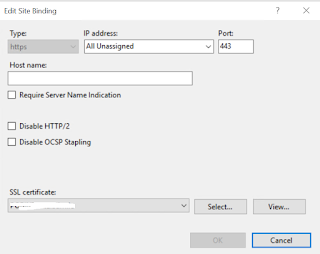
I remembered that I hadn't reconfigured the Site Bindings in IIS to use the new NDES SSL certificate. Once I did that and executed another IIS Reset, the certificates started to fly and the customer was back in business with SCEP and 802.1x authentication.
I hope this helps. Until next time......

























No comments:
Post a Comment