(First published in Dec 2018 but I was too early so I withdrew the post 😃)
This has been one of the most requested Intune features for quite some time and, yesterday, it was released as a public preview in Intune 1901. What is it all about? You can find the official documentation here
For many years now we have relied on Microsoft to provide guidance on the security settings that we should configure. In the on-premise Active Directory world we don't want to analyse every possible GPO that is available. That's why we implement the Microsoft security baselines as a starting point and then we change individual settings as required. Microsoft have now provided Windows 10 security baselines for the Intune MDM-managed world. I tested it today and it's really easy to implement. It works well too.
Remember that this is a public preview only and is only supported with Windows 10 version 1809 and later. It is not yet recommended for production.
So where do we start? In the Azure portal, navigate to All Services and search for Intune. Select Security Baselines (Preview).
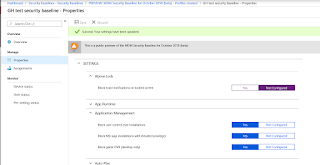
Launch Security Baselines and we can see the Preview: MDM Security Baseline for October 2018 (beta).
Drill into the baseline. Click Create profile.
Enter some details (Name and Description) for your baseline (profile). The platform and baseline drop-down arrows are grayed out. These will probably become available as more baselines are released for different Windows 10 versions.
Have a look at the Settings. These are the kind of security heading that you would expect.
"Block toast notifications on locked screen" is enabled in the baseline. I'll check for that in my test computer in a minute.
The Browser settings look secure.....
....and these are the Device Lock settings. See that we will prevent the reuse of the previous 24 passwords. That's pretty secure. I'll check that on my test client also.
Once the profile has been created it should be assigned to a group (of devices or users).
Ok, on my test device, I've initiated a manual sync. Otherwise I'd have to wait up to 8 hours.
I've generated an MDM Diagnostics report.
These are the results. I can see that DevicePasswordHistory is now configured for 24.
AllowToasts is now disabled.
So what happens if I make a change to a baseline? Let's change the toast notification setting to Not Configured.
After a manual sync I can see that this setting is no longer managed.
I can see a lot of potential with this feature. Try it out (although not in production yet).
Until next time......
Monday 17 December 2018
Thursday 6 December 2018
Wake on LAN in ConfigMgr 1810 and 802.1x authentication
I recently carried out some testing on the new Wake on LAN feature of ConfigMgr 1810 and published the result in this blog post. One of the things I pointed out was that the feature was not supported using 802.1x authentication. I wondered why so I carried out some additional research.
As with all Microsoft support statements, just because something is not supported doesn't mean that it will not work. It's either untested or will not work in all scenarios. This is the case with WoL and 802.1x authentication.
802.1x is a standard for port-based network access control that provides authenticated network access to 802.11 wireless networks and wired Ethernet networks. Port-based network access control uses the physical characteristics of a switched LAN infrastructure to authenticate devices that are attached to a LAN port and to prevent access to that port in cases where the authentication process fails. One of the features of 802.1x is that devices are quarantined when they are turned off. Therefore the switch ports becomes blocked in both directions and prevents the WoL magic packet from being delivered - a chicken and egg situation.
I figured that this couldn't a new problem and that it would be possible to overcome this in the enterprise. I was right. I researched the main networking vendors and found that they had solutions.
Cisco
The 802.1X authentication with Wake-on-LAN (WoL) feature solves the problem. When a host that uses WoL is attached through an 802.1X port and the host powers off, the 802.1X port becomes unauthorized. The port can only receive and send EAPOL packets, and WoL magic packets cannot reach the host. When the PC is powered off, it is not authorized, and the switch port is not opened.
When the switch uses 802.1X authentication with WoL, the switch forwards traffic to unauthorized 802.1X ports, including magic packets. While the port is unauthorized, the switch continues to block ingress traffic other than EAPOL packets. The host can receive packets but cannot send packets to other devices in the network.
https://www.cisco.com/en/US/docs/ios-xml/ios/sec_usr_8021x/configuration/15-2mt/sec-ieee-wake-lan-supp.html
HP
The aaa port-access controlled-direction in command allows Wake-on-LAN traffic to be transmitted on an 802.1X-aware egress port that has not yet transitioned to the 802.1X authenticated state; the controlled-direction both setting prevents Wake-on-LAN traffic to be transmitted on an 802.1X-aware egress port until authentication occurs.
Note: Although the controlled-direction in setting allows Wake-on-LAN traffic to traverse the switch through unauthenticated 802.1X-aware egress ports, it does not guarantee that the Wake-on-LAN packets will arrive at their destination. For example, firewall rules on other network devices and VLAN rules may prevent these packets from traversing the network.
http://h22208.www2.hpe.com/eginfolib/networking/docs/switches/WB/15-18/5998-8152_wb_2920_asg/content/ch13s05.html
Aruba Networks (not Procurve)
In Aruba AOS (not Procurve) there is a MAC pinning feature which basically adds a static MAC address to the port and associates it to the authentication as a pinned-MAC. All traffic to that MAC address would be pre-authenticated and anything else would need to be authenticated.
Summary
For enterprise grade edge switches I would expect a solution for this problem. You may not be so lucky with low end switches and your mileage may vary. That's why this solution is not officially supported by Microsoft.
As with all Microsoft support statements, just because something is not supported doesn't mean that it will not work. It's either untested or will not work in all scenarios. This is the case with WoL and 802.1x authentication.
802.1x is a standard for port-based network access control that provides authenticated network access to 802.11 wireless networks and wired Ethernet networks. Port-based network access control uses the physical characteristics of a switched LAN infrastructure to authenticate devices that are attached to a LAN port and to prevent access to that port in cases where the authentication process fails. One of the features of 802.1x is that devices are quarantined when they are turned off. Therefore the switch ports becomes blocked in both directions and prevents the WoL magic packet from being delivered - a chicken and egg situation.
I figured that this couldn't a new problem and that it would be possible to overcome this in the enterprise. I was right. I researched the main networking vendors and found that they had solutions.
Cisco
The 802.1X authentication with Wake-on-LAN (WoL) feature solves the problem. When a host that uses WoL is attached through an 802.1X port and the host powers off, the 802.1X port becomes unauthorized. The port can only receive and send EAPOL packets, and WoL magic packets cannot reach the host. When the PC is powered off, it is not authorized, and the switch port is not opened.
When the switch uses 802.1X authentication with WoL, the switch forwards traffic to unauthorized 802.1X ports, including magic packets. While the port is unauthorized, the switch continues to block ingress traffic other than EAPOL packets. The host can receive packets but cannot send packets to other devices in the network.
- When you configure a port as unidirectional by using the dot1x control-direction in interface configuration command, the port changes to the spanning-tree forwarding state. The port can send packets to the host but cannot receive packets from the host.
- When you configure a port as bidirectional by using the dot1x control-direction both interface configuration command, the port is access-controlled in both directions. The port does not receive packets from or send packets to the host.
https://www.cisco.com/en/US/docs/ios-xml/ios/sec_usr_8021x/configuration/15-2mt/sec-ieee-wake-lan-supp.html
HP
The aaa port-access controlled-direction in command allows Wake-on-LAN traffic to be transmitted on an 802.1X-aware egress port that has not yet transitioned to the 802.1X authenticated state; the controlled-direction both setting prevents Wake-on-LAN traffic to be transmitted on an 802.1X-aware egress port until authentication occurs.
Note: Although the controlled-direction in setting allows Wake-on-LAN traffic to traverse the switch through unauthenticated 802.1X-aware egress ports, it does not guarantee that the Wake-on-LAN packets will arrive at their destination. For example, firewall rules on other network devices and VLAN rules may prevent these packets from traversing the network.
http://h22208.www2.hpe.com/eginfolib/networking/docs/switches/WB/15-18/5998-8152_wb_2920_asg/content/ch13s05.html
Aruba Networks (not Procurve)
In Aruba AOS (not Procurve) there is a MAC pinning feature which basically adds a static MAC address to the port and associates it to the authentication as a pinned-MAC. All traffic to that MAC address would be pre-authenticated and anything else would need to be authenticated.
Summary
For enterprise grade edge switches I would expect a solution for this problem. You may not be so lucky with low end switches and your mileage may vary. That's why this solution is not officially supported by Microsoft.
Tuesday 4 December 2018
Major Wake on LAN improvement with SCCM 1810
This
has been an eagerly awaited feature. It's been on Uservoice since May of last
year and has now been released to production in SCCM 1810. You can now wake up
clients from the Configuration Manager console, even if the client isn't on the
same subnet as the site server. The site server uses the client notification channel
to identify another client that's awake on the same remote subnet. The awake
client then sends a wake on LAN request (magic packet). I must admit that I was
a bit sceptical about this but I've now tested it in my lab and it just works - I was
pleasantly surprised.
Wake on LAN has been a difficult solution to implement with Configuration Manager for many years. It has worked perfectly on the local subnet but could be problematic for remote subnets.
Why is that?
Let's start but by discussing exactly what it is. Wake-on-LAN (sometimes abbreviated WoL) is the industry standard for waking computers up remotely from a very low power mode. WoL is usually configured through the network card’s firmware, so you don’t need specific software to enable it. Support for Wake-on-LAN is now pretty universal and you can expect that the functionality would be available on any computer purchased in the last ten years.
Wake-on-LAN-enabled computers wait for a “magic packet” to arrive that includes the network card’s MAC address in it. These magic packets are often sent by a management solution (e.g. ConfigMgr). The typical ports used for WoL magic packets are UDP 7 and 9. Magic packets are usually sent over the entirety of a network and contain the subnet information, network broadcast address, and the MAC address of the target computer’s network card.
WoL magic packets are not routable so configuring the solution for remote subnets has always been problematic. Microsoft previously developed the wake-up proxy to help with this situation but that solution also carried a health warning. In certain circumstances (i.e. when you're using port-security) wake-up proxy could lead to disruption and loss of service. Wake-up proxy caused the network switch to believe that a different network adapter was using the port than the one that was registered. This behaviour is known as a MAC flap and is unusual for standard network operation. Some network monitoring tools look for this behaviour and can assume that something is wrong. Consequently, these monitoring tools can generate alerts or shut down ports when you use wake-up proxy. It was recommended not to use wake-up proxy if the network monitoring tools and services did not allow MAC flaps.
With this new solution in 1810 the site server uses the client notification channel to identify another client that's awake on the same remote subnet. It's all pretty straightforward to configure so let's have a look. Remember this solution allows you to implement a remote WoL solution without having to configure any networking.
SCCM side:
This part hasn't changed from the original WoL configuration.
Scroll down in the list to find Wake on Magic Packet. Change the value to Enabled. The other “Wake on” settings are not required.
Right click on the computer you want to wake up. Select the Client Notification channel. See the new Wake up option. (The same action is available on a specific collection. The site tries to wake up any client in that collection that's asleep.)
ConfigMgr is pretty smart here and will know if there is no other client computer awake on the remote subnet.
I'm in luck. I have a computer that is already awake on the remote subnet. Remember I didn't configure any kind of proxy computer. I merely ensured that the NICs were configured correctly for WoL.
Success. The magic packet is detected almost immediately on client 2 (see the text in the WoL monitor) and immediately wakes up client1.
Wake on LAN has been a difficult solution to implement with Configuration Manager for many years. It has worked perfectly on the local subnet but could be problematic for remote subnets.
Let's start but by discussing exactly what it is. Wake-on-LAN (sometimes abbreviated WoL) is the industry standard for waking computers up remotely from a very low power mode. WoL is usually configured through the network card’s firmware, so you don’t need specific software to enable it. Support for Wake-on-LAN is now pretty universal and you can expect that the functionality would be available on any computer purchased in the last ten years.
Wake-on-LAN-enabled computers wait for a “magic packet” to arrive that includes the network card’s MAC address in it. These magic packets are often sent by a management solution (e.g. ConfigMgr). The typical ports used for WoL magic packets are UDP 7 and 9. Magic packets are usually sent over the entirety of a network and contain the subnet information, network broadcast address, and the MAC address of the target computer’s network card.
WoL magic packets are not routable so configuring the solution for remote subnets has always been problematic. Microsoft previously developed the wake-up proxy to help with this situation but that solution also carried a health warning. In certain circumstances (i.e. when you're using port-security) wake-up proxy could lead to disruption and loss of service. Wake-up proxy caused the network switch to believe that a different network adapter was using the port than the one that was registered. This behaviour is known as a MAC flap and is unusual for standard network operation. Some network monitoring tools look for this behaviour and can assume that something is wrong. Consequently, these monitoring tools can generate alerts or shut down ports when you use wake-up proxy. It was recommended not to use wake-up proxy if the network monitoring tools and services did not allow MAC flaps.
With this new solution in 1810 the site server uses the client notification channel to identify another client that's awake on the same remote subnet. It's all pretty straightforward to configure so let's have a look. Remember this solution allows you to implement a remote WoL solution without having to configure any networking.
SCCM side:
This part hasn't changed from the original WoL configuration.
- In the ConfigMgr console navigate to Administration > Site Configuration > Sites.
- Select the site, right click and select Properties.
- Click the Wake on LAN tab
- Check the box next to "Enable Wake On LAN for this site:"
- Select a WoL transmission method
- Click on Advanced to see the WoL transmission options. To make the solution more reliable you may choose to increase the number of retries.
- Select the Ports tab of the site properties. The default WoL port in ConfigMgr is 9. For security reasons Microsoft recommends that you change this to a more obscure port (I've left it at 9 for now).
- Save the configuration
Log files
You will notice that two new log files are created on the site server. There are no client-side log files for WOL.
- WolCmgr.log: Contains information about which clients need to be sent wake-up packets, the number of wake-up packets sent, and the number of wake-up packets retried.
- Wolmgr.log: Contains information about wake-up procedures, such as when to wake up deployments or deployments that are configured for WOL.
Client side configuration
This involves configuration of the NIC properties. Right
click on your network card and choose Configure, then click on the Advanced
tab.
Scroll down in the list to find Wake on Magic Packet. Change the value to Enabled. The other “Wake on” settings are not required.
Click the Power Management tab, and make sure the "Allow this device to wake
the computer” and “Only allow a magic packet to wake the computer” boxes are
enabled.
You need to ensure that these options are set for all the computers you will need to wake up. That could be a pain to do manually. Terence has a good blog post on creating a ConfigMgr CI for this.
Testing
Now let's have a
look at the new functionality. What do you need?
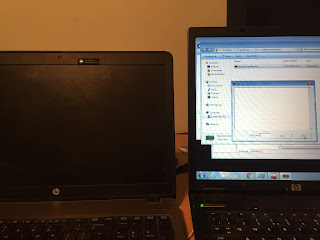
This is the "remote subnet" of my lab. I have two laptops with the NICs configured for WoL and the ConfigMgr client installed.
- Client 1 is turned off
- Client 2 is turned on with a WoL monitor running. Client 2 will receive the magic packet and will turn client 1 on
Right click on the computer you want to wake up. Select the Client Notification channel. See the new Wake up option. (The same action is available on a specific collection. The site tries to wake up any client in that collection that's asleep.)
ConfigMgr is pretty smart here and will know if there is no other client computer awake on the remote subnet.
I'm in luck. I have a computer that is already awake on the remote subnet. Remember I didn't configure any kind of proxy computer. I merely ensured that the NICs were configured correctly for WoL.
Success. The magic packet is detected almost immediately on client 2 (see the text in the WoL monitor) and immediately wakes up client1.
The WoL monitor shows details of the magic packet. See how I configured the port to match the ConfigMgr WoL port.
Remember that your required deployments continue to work as normal (applications, task sequences and software updates).
I was amazed at how well this works (with minimal effort). I'll now implement this at my customer sites.
There are some limitations to the solution
I was amazed at how well this works (with minimal effort). I'll now implement this at my customer sites.
Limitations
There are some limitations to the solution
- At least one client in the target subnet must be awake.
- IPv6 is not supported (I presume this means it won't work over Direct Access).
- 802.1x network authentication is not supported.
Until next time......
Subscribe to:
Posts (Atom)