A ConfigMgr admin
has to be a good all-rounder and be knowledgeable in a wide variety of
technologies. This came to mind when I was compiling this list of tips
for setting up a Cloud Management Gateway. The list includes tips on DNS,
certificates and Azure permissions. If you have any tips please add to the list
by adding a comment here (or DM me on Twitter). I'll add your tip and your
Twitter handle.
So let's start. The
tips are in the form of questions.
What CName record do
I need?
When we
create a ConfigMgr CMG we will actually be creating a custom cloud service in
Azure. This needs to be unique so we need to see if we can find an available
name before we continue.
In the Microsoft Azure portal select Create a Resource, > type Cloud Service > Create. In the DNS name field type the desired domain name – I want to use “GerryHampson”. Note
that the full service name would be GerryHampson.cloudapp.net
Don’t
continue to create the service. We just want to make sure that the name is
available. I always
use a public SSL certificate for the CMG service and I know I won’t be able to
get a certificate with GerryHampson.CLOUDAPP.NET as the Subject Name.
Therefore, we have to be clever. We create a canonical name record (CNAME) in
our DNS records to create an alias for the cloud management gateway service to
a friendly name.
We’ll use an externally routable domain that I own. See where I’ve
created the CName record. Now I can use GerryHampson.EMSLAB.IE as the Subject
Name for my SSL certificate for the CMG service. This will direct requests to
GerryHampson.CLOUDAPP.NET.
Can I use a Wildcard
cert?
Yes you can but don't get alarmed when you select the certificate in the Cloud Management Gateway wizard.
You'll see this warning telling you that the certificate has a wildcard DNS name and you must change it to a proper FQDN. You must delete the wildcard asterisk and type the FQDN e.g. GerryHampson.EMSLAB.IE.
This automatically
changes the value below to (for example) GerryHampson.CLOUDAPP.NET
What file format do
I need for the CMG certificate?
When creating a CMG we will need an SSL certificate for authentication. I always us a public SSL certificate for this. We need this certificate to have a .pfx extension and be associated with a private key. No other
file extension will do.
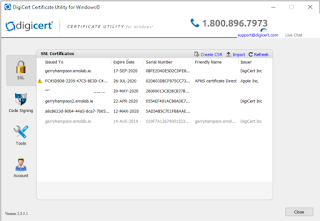
This is usually pretty easy and I normally use DigiCert for my SSL certificates. They provide a utility which you can download here
- Run Digicert tool and navigate to the SSL section
- Select Create CSR
- Enter Common Name, Organization, City and Country
- Click to Generate a Certificate Signing Request (CSR)
- The CSR is generated. You can copy the CSR or save to a file which you can upload on the DigiCert portal when you are processing your order.
- You'll have to confirm contact details, then you get an email confirming that your certificate has been issued and is ready for download.
- Download the certificate (which comes in a .crt file format)
- Import the certificate to the tool to finish the process which automatically adds the private key. Note that you have to finish the process on the same computer as you generated the CSR. Otherwise you won't have access to the private key.
- Then export to the .PFX format. Highlight the certificate and select Export Certificate.
- Choose to export the private key.
- Enter a password for the certificate and the PFX file is generated.
- Browse to the PFX file in the CMG wizard.
That was easy. However what if you haven't got control over the whole process. I've been in situations where the customer has already generated the SSL certificate.
These are the files I am often given. Note that there is no PFX file. We can work with this though. You'll need the .crt
and .key files.
In this case you can use Open SSL for Windows. Download from here. This allows us to convert SSL certificates to different formats.
Run the tool using this command.
pkcs12 -export -out <Path>\MyCert.pfx -inkey <Path>\MyCert.key -in <Path>\MyCert.crt
The tool accepts the .crt and .key files as input parameters and outputs a .pfx file. It asks you for a password before it generates the file.
What Azure
permissions do I need?
There are two distinct permissions that we need to worry about.
- The account that you use to configure the Azure services must be a Global Administrator on the tenant. This is to allow you to create app registrations for the server and client app.
- The Microsoft documentation tells us that the account that you use to create the CMG must be a subscription administrator. However this role doesn't actually exist. The account must be an Owner of the subscription (Contributor is not enough).
This is what you see if the account is not an owner of the subscription.
What is Enhanced HTTP?
In previous CMG deployments we had to deploy a full PKI infrastructure as the Management Point had to be configured for HTTPS before we could allow CMG traffic.
See that we can only allow CMG traffic if we select HTTPS. Although this is still the preferred way to secure the solution many customers were unhappy with this overhead.
We can select to Use Configuration Manager generated certificates for HTTP site systems. Now Azure AD-joined devices can communicate with a management point configured for HTTP. The site server generates a certificate for the management point allowing it to communicate via a secure channel.
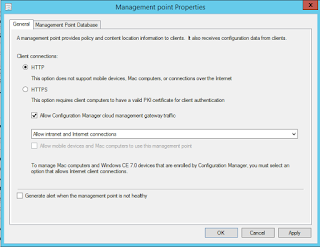
Now we can allow CMG traffic without configuring the Management Point for HTTPS.
How can we test that the CMG is working?
On the server side use the CMG Connection Analyzer
You should see that all components are configured and working together successfully.
On the client side you should first ensure that the client knows about the CMG. Execute this PowerShell cmdlet:
gwmi -namespace root\ccm\locationservices -class SMS_ActiveMPCandidate
It will display all available management points that the client is aware of. The CMG should listed.
- Move the client from the intranet to the internet
- Check ClientLocation.log to see that the client is domain-joined but on the internet
- In the ConfigMgr console open the All Desktops and Servers device collection
- Add the field Device Online from Internet and look for True
- Add the field Device Online Management Point and look for the CMG MP
- You should now be able to manage this device through the ConfigMgr fast notification channel even though it’s over the internet.
- In the ConfigMgr console right click the client > Client Notification > Collect hardware inventory
- On the client the InventoryAgent.log file shows that inventory is being collected. You should also be able to see this in the datalder.log file in ConfigMgr
Does the date and time matter?
Oh yes it does. We have deployed several CMGs for customers at this stage and we’ve generally not had any issues. However we had one difficult environment. The Primary Site server sat behind two firewalls and a web filter so we had to work closely with the network team to arrange the required network connectivity. We “thought” everything was in place but the CMG wizard still failed -
- “with status code 'Forbidden' and reason phrase 'Server failed to authenticate the request. Make sure the value of Authorization header is formed correctly including the signature”.
I got some help from the product group on this one. They'd seen this in testing and said that the error was probably due to a time difference between the service connection point and the real world. A SAS URL is created based on the time on the service connection point and if the time is ahead then the deployment package is not yet valid on Azure.
Sure enough we checked the time and it was slightly out. Setting the clock back did the business and we could complete the wizard and deploy the CMG.
Any more tips?
Have you any CMG tips? Let me know and I'll add them. Thanks.
Until next time....
Do we have to enable some Azure resource providers first? (@RahulJindal)
Yes, the Microsoft.ClassicCompute and Microsoft.Storage resource providers are classic services and are not registered by default. They must be registered within the Azure subscription.
Search for your Subscription and select Resource providers.
Locate Microsoft.ClassicCompute and Microsoft.Storage and register them.
These resource providers are not available with a Cloud Service Provider (CSP) subscription. Therefore CMG cannot be deployed using a CSP subscription.