This is a quick follow up to my recent post where I discussed an issue my customer was having with an unwanted reboot. We narrowed this down to Microsoft Defender Application Control in Microsoft Endpoint Manager, "Application control code integrity policies" being set, even to Audit Only.
I referred my customer to Peter van der Woude's post, where Peter talks about creating a custom code integrity policy using OMA-URI and the Application Control CSP. I had previously tested the solution successfully was I was quite happy to recommend it. My customer also successfully tested the solution in their lab but ran into difficulty when implementing in a production pilot. The policy status for the pilot devices was "Not applicable".
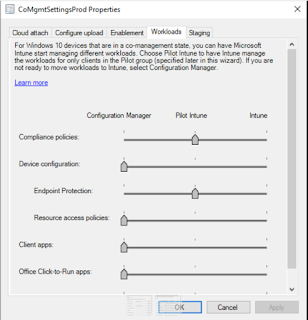
This was a little unusual but it was obvious when I figured out why. All testing was carried out in an Intune only environment. However, these devices were co-managed with the following settings.
The Endpoint Protection workload had been moved to Intune pilot. That worked well for Microsoft Defender policies. However the new policy (as per Peter's post) was a device configuration profile. This workload was still set to ConfigMgr and therefore the policy was not applicable to the devices. This was easily solved by moving the device configuration workload slider to Intune. Then the Intune policy applied as expected.
The only thing we had to worry about was that the customer was using some ConfigMgr configuration baselines and still wanted them managed by ConfigMgr.
Luckily Microsoft provides a solution for that. We selected "Always apply this baseline even for co-managed clients".
I hope this helps if you encounter a similar situation.
Until next time......