On premise Mobile Device Management is a new feature released in Configuration Manager 1511. It allows you to manage mobile devices without synchronising your user accounts to Azure. Also devices enrol directly with the on premise infrastructure unlike regular MDM which requires each device to enrol with Intune. Although devices do not contact Intune directly you must still have an Intune subscription and licenses to deploy this solution.
Currently the solution only supports Windows 10 devices.
This is quite a complex solution with many moving parts. I've added a second Configuration Manager server to my lab to enable it.
You'll find the official Microsoft documentation here. I've deployed by getting nuggets of information from various other sources. I'll share all that information here. Kent Agerlund and Panu Saukko provide the bulk of the information in a blog post that they published in late 2015 (see the references section at the bottom of this post).
Beware - this is a pretty long blog post.
The following are the high level steps required (remember this was my lab environment so I had to start from scratch):
PKI (on my Domain Controller)
- Install PKI
- Configure CRL and CRLDP
- Create Certificates
ConfigMgr roles (my second CM server)
- Add Management Point and configure for HTTPS
- Add Distribution Point and configure for HTTPS
- Add Enrollment Point and Enrollment Proxy Point
- Registry fix (SendTrustedIssuerList)
- User collection
- Add Intune subscription (require Service Connector)
- Enable Windows enrollment
- Create Enrollment Profile (Client Settings)
- Certificates
- Work access > Connect
Install PKI
You will need the following role services:
- Certification Authority
- Certification Authority Web Enrollment
- Certification Authority Web Service
Note that the Certification Authority and the Certification Authority Web Service cannot be installed simultaneously. You must complete the CA setup first and then add the CA Web Service.
Configure CRL and CDP
When Windows 10 clients communicate over HTTPS they automatically check to see if the certificate they are using has been revoked. They find this information in the CRL (Certificate Revocation List). The CRL comes in the form of two files stored in a virtual directory which is accessible to the Windows 10 clients (full and delta CRL files).
The CRL location (CRL Distribution Point) must be configured in the CA so that it is included in all issued certificates. If you don't get this bit right you will not be able to successfully implement on premise MDM. You have to do this configuration BEFORE you issue your certificates.
(I haven't personally tested this but it looks like, if you are already configured to use https, you will have to replace the MP and DP certificates after you carry out this work).
Follow this Microsoft blog to configure your CRLDP.
Creating a Certificate Revocation List Distribution Point for Your Internal Certification Authority
The CRL location (CRL Distribution Point) must be configured in the CA so that it is included in all issued certificates. If you don't get this bit right you will not be able to successfully implement on premise MDM. You have to do this configuration BEFORE you issue your certificates.
(I haven't personally tested this but it looks like, if you are already configured to use https, you will have to replace the MP and DP certificates after you carry out this work).
Follow this Microsoft blog to configure your CRLDP.
Creating a Certificate Revocation List Distribution Point for Your Internal Certification Authority
The steps are as follows:
Create CRL DNS record
Create file share and virtual directory
Publish CRL to CDP
Create Certificates
As I previously said there are numerous working parts to this solution. We will require an additional Management Point and Distribution Point (configured to communicate via HTTS). Therefore we need a few certificates. The process for this is the same as we use for implementing Internet Based Client Management. I used the following certificates for my lab:
PKI Certificate Requirements for Configuration Manager
SCCM 2012 Internet based client management
How to install a ConfigMgr Client on a WORKGROUP computer, when the ConfigMgr Site is in Native Mode.
The main steps are as follows:
Add Management and Distribution Points and configure for HTTPS
As I previously said there are numerous working parts to this solution. We will require an additional Management Point and Distribution Point (configured to communicate via HTTS). Therefore we need a few certificates. The process for this is the same as we use for implementing Internet Based Client Management. I used the following certificates for my lab:
- Distribution Point Client Certificate
- Management Point Web certificate
- Client certificate
PKI Certificate Requirements for Configuration Manager
SCCM 2012 Internet based client management
How to install a ConfigMgr Client on a WORKGROUP computer, when the ConfigMgr Site is in Native Mode.
The main steps are as follows:
- Create web certificate template
- Create DP certificate template
- Create client certificate template
- Generate web certificate
- Generate DP certificate
- Generate client certificate
- Assign the web certificate in IIS and bind to https (second Configuration Manager server)
Add Management and Distribution Points and configure for HTTPS
See MP Prerequisites
See DP Prerequisites
See my previous blog posts for installing additional Management and Distribution Points
Management Point
Distribution Point
This time we need to configure for https
Select "Specify an FQDN for this site system for use on the Internet. If we were configuring this for IBCM we would use an external FQDN here. However this is for on premise only so just enter the name of the server.
Select HTTPS (Allow intranet and internet connections). Select "Allow mobile devices to connect to the DP".
Import the DP certificate we created earlier.
Choose HTTPS (allow intranet and internet connections) for the MP.
After the roles have been added edit the site properties and set the Trusted Root CA.
Add Enrollment Point and Enrollment Proxy Point
Now select to add new site system roles on the second server.
Add the Enrollment Point and Enrollment Proxy Point roles in a default configuration.
(don't forget to install the prerequisites first - you can find them here)
(don't forget to install the prerequisites first - you can find them here)
Registry fix (SendTrustedIssuerList)
There is a known issue when using SSL certificate authentication with Windows Server 2012. You can read about this issue here.
Apply the registry fix shown if required.
User collection
You must select a user collection when you create the Intune subscription. For MDM using Intune I always create an "Intune users" collection. The users in this collection will be allowed to enrol devices with Intune. If you are just configuring on premise MDM only, you must choose a user collection, but it doesn't matter which one you pick. This has no effect. A count of licensing is tracked in Intune (rather than specific users).
Add Intune subscription (require Service Connector)
Although this is an on premise solution you will still need to add the Intune subscription.
Enable Windows enrolment
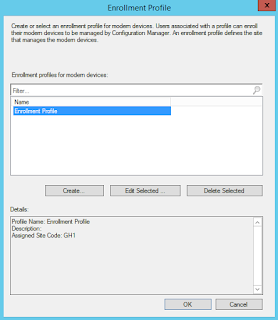
Create Enrollment Profile (Client Settings)
Export the trusted root certificate to a .cer file.
Now navigate to Assets and Compliance > Compliance \settings > Company Resource Access.
Right click and create a certificate profile.
Enter a suitable name and choose "Trusted CA certificate".
Browse to the .cer file. Ensure that the Destination store is Root.
Choose Windows 10.
Finish the wizard to create the certificate profile.
Now enable enrolment in your client settings. Click to "Set Profile".
Click to create an Enrolment profile.
Enter a suitable name, choose the site code and verify the certificate profile.
Click OK to finish and create the enrolment profile.
Client
OK, now let's move to the client.
Import the certificates we created earlier (Trusted root cert and client cert)
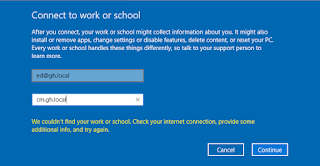
Enter your local account details.
The first attempt will fail. Now enter your enrollment server name.
This looks hopeful. Enter the password.
Choose whether or not you want this password remembered.
We're connecting........
.....and we've connected.
The device is now enrolled using our on premise infrastructure only.
Click on Info to see the sync status
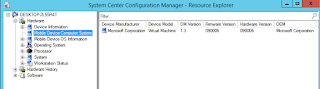
Windows 10 computers now appear in the ConfigMgr console as mobile devices.
We can right click and retire the devices from the console.
The device becomes unmanaged almost immediately.
Issues encountered
1. You must ensure that you have published the CRL in the CRLDP before issuing the client certificates. Otherwise you will have to re-create the certificate.
This is a healthy certificate showing the CRL DP location (see the URL at the bottom).
If you don't do this you will be able to enrol but the device will never sync or appear in the Configuration Manager console.
You will receive an error 0x800728f in this case.
I did carry out the work in advance but I still had the issue. I tested by browsing to the CRL DP location but I couldn't download the CRL files. I could however browse to the virtual directory. I noticed that somehow there was a space at the beginning of the CRL filenames. Once I removed the space I was able to sync correctly.
2. Trusted Root certificate
You will receive this error if you have installed the client certificate but not the Trusted Root certificate on the Windows 10 device.
Now see how to create Windows 10 Provisioning Packages with Configuration Manager.
References:
Install and Configure on-prem mobile device management (MDM) with ConfigMgr vNext TP3 (Kent Agerlund & Pan Saukko)
Creating a Certificate Revocation List Distribution Point for Your Internal Certification Authority
PKI Certificate Requirements for Configuration Manager
SCCM 2012 Internet based client management (System Centre Dudes)
How to install a ConfigMgr Client on a WORKGROUP computer, when the ConfigMgr Site is in Native Mode. (Peter van der Woude)








































Thanks for sharing this Gerry. I am looking forward to implement it my self!
ReplyDeleteIsn't there a solution for mass enrollement? If I understood it correctly, we still need to workplace join each mobile device individually.
No worries Stephane. Yes, currently you have to enrol each device individually.
DeleteNope, thats not correct. There's a bulk enrollment Feature, which is quite easy to rollout. You can configure the Profile in Configmgr Console which creates a .ppkg - On the Client, double click the .ppkg and you're done. No User Logon necessary!!
ReplyDeleteStrange: No User Logon means no license check, but it definitely works. Second: I see a huge security Problem here: Just send some Intune Profile to anyone, double click is enough to set the machine under foreign management...
Regards, Michael
I hear you Michael. To me that is provisioning, not bulk enrollment. The user still has to do something on each device. They're just doing it with a package. Apple DEP is bulk enrollment.
Deletethanks for sharing your xp gerry, i am looking for a complete mdm without usung or any dependenco on intune and want to have it all in our datacenter...is there any solution related to sccm...plugin...third party...?
ReplyDeleteNo, Intune is the only solution that integrates with SCCM.
Delete