This is becoming very popular and many of my customers have recently made the switch. It seems like a no-brainer, especially if you have purchased Microsoft 365 E5 licenses.
This information should help you to plan and implement a migration from another endpoint protection solution.
Is Microsoft Defender Antivirus free?
It is, kind of. Microsoft Defender Antivirus is a core component of Windows 10. It's built into the operating system and is included in the cost of Windows. This is often good enough for a home user but certainly not for an enterprise organization. Defender AV needs to be managed and you must license the management tools. Microsoft Endpoint Manager (SCCM or Intune) are the favourites here.
What is Defender for Endpoint?
I've found that this is the most confusing part for customers. Defender for Endpoint (DfE), formerly Defender Advanced Thread Protection (ATP) is not Defender Antivirus. It's an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. Data from Defender antivirus can be consumed and used by DfE by onboarding devices independently to the service. You can currently access DfE (until 6th July 2021) using the Microsoft Defender Security Center
https://securitycenter.windows.com/ (see next question).
What is Microsoft 365 Defender?
This is an integrated solution including the following:
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Cloud App Security
You can access the M365 Defender portal at https://security.microsoft.com/
The Microsoft Defender Security Center standalone portal will no longer be available from 6th July 2021.
What license do I need for Defender for Endpoint for my workstations/laptops?
Microsoft Defender for Endpoint requires one of the following Microsoft volume licensing offers:
- Windows 10 Enterprise E5
- Windows 10 Education A5
- Microsoft 365 E5 (M365 E5) which includes Windows 10 Enterprise E5
- Microsoft 365 A5 (M365 A5)
- Microsoft 365 E5 Security
- Microsoft 365 A5 Security
- Microsoft Defender for Endpoint (this is a standalone offering where you don't have any of the above subscriptions)
These are user based. Eligible licensed users may use Microsoft Defender for Endpoint on up to five concurrent devices.
I have Microsoft 365 E5 licenses for all my users. Does this cover servers?
No, in this case you will need Microsoft Defender for Endpoint for Server (one per covered server). This is also covered with "Azure Security Center with Azure Defender enabled".
Can I just purchase Microsoft Defender for Endpoint for Server only?
No. Customers may acquire server licenses (one per covered server Operating System Environment (OSE)) for Microsoft Defender for Endpoint for Servers if they have a combined minimum of 50 licenses for one or more of the following user licenses:
- Microsoft Defender for Endpoint
- Windows E5/A5
- Microsoft 365 E5/A5
- Microsoft 365 E5/A5 Security
What else should I consider when migrating to a Microsoft Defender solution?
It's possible that this migration is not as simple as just switching to a new antivirus solution. There are a number of considerations.
- Will you also be using Defender for Endpoint? This is recommended.
- How will you manage Defender antivirus settings? It is recommended to use SCCM or Intune antimalware policies.
- Note that Intune does not manage servers so you need to consider that.
- Is your current solution providing more than antivirus functionality, which you must replace before decommissioning? Windows Firewall configuration is common, for example.
Can Microsoft Defender Antivirus and non-Microsoft antivirus/antimalware solutions co-exist?
Microsoft Defender Antivirus is automatically enabled and installed on endpoints and devices that are running Windows 10. But what happens when another (non-Microsoft) antivirus/antimalware solution is used? It depends on whether you're using Microsoft Defender for Endpoint together with your antivirus protection.
- In active mode, Microsoft Defender Antivirus is used as the antivirus app on the machine. Management products will apply. Files are scanned and threats remediated, and detection information are reported in your configuration tool.
- In passive mode, Microsoft Defender Antivirus is not used as the antivirus app, and threats are not remediated by Microsoft Defender Antivirus. Files are scanned and reports are provided for threat detections that are shared with the Microsoft Defender for Endpoint service.
- When EDR in block mode is turned on (in Microsoft Defender for Endpoint) and Microsoft Defender Antivirus is not the primary antivirus solution, it will detect and remediate malicious items. EDR in block mode requires Microsoft Defender Antivirus to be enabled in either active mode or passive mode.
- When disabled, Microsoft Defender Antivirus is not used as the antivirus app. Files are not scanned and threats are not remediated. Disabling/uninstalling Microsoft Defender Antivirus is not recommended in general; if possible, keep Microsoft Defender Antivirus in passive mode if you are using a non-Microsoft antimalware/antivirus solution.
- If you are enrolled in Microsoft Defender for Endpoint and you are using a third-party antimalware product, then passive mode is enabled. The service requires common information sharing from Microsoft Defender Antivirus service in order to properly monitor your devices and network for intrusion attempts and attacks.
- When Microsoft Defender Antivirus is in passive mode, you can still manage updates for Microsoft Defender Antivirus; however, you can't move Microsoft Defender Antivirus into active mode if your devices have an up-to-date, non-Microsoft antivirus product that is providing real-time protection from malware.
- When Microsoft Defender Antivirus is disabled automatically, it can be re-enabled automatically if the protection offered by a non-Microsoft antivirus product expires or otherwise stops providing real-time protection from viruses, malware, or other threats.
The following table summarizes what happens with Microsoft Defender Antivirus when non-Microsoft antivirus/antimalware solutions are used together, with or without Microsoft Defender for Endpoint.
Notes:
1. On Windows Server, version 1803 or newer, or Windows Server 2019, Microsoft Defender Antivirus does not enter passive mode automatically when you install a non-Microsoft antivirus product. you can set Microsoft Defender Antivirus to passive mode by setting the following registry key
Path: HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection
Name: ForceDefenderPassiveMode
Type: REG_DWORD
Value: 1
2. Passive mode is not supported on Windows Server 2016. If you are using a non-Microsoft antivirus product, you cannot run Microsoft Defender Antivirus in either passive mode or active mode. In such cases, disable/uninstall Microsoft Defender Antivirus manually.
How can Defender antivirus be configured and managed?
Microsoft Endpoint Manager (SCCM or Intune) is my tool of choice for managing these settings. Let's have a look at SCCM first.
- The Endpoint Protection Point is a site system role that must be added.
- Afterwards, we can see Endpoint Protection status under Monitoring > Security.
- Create antimalware policies and deploy to device collections. This includes items like scheduled scans, scan settings, real-time protection and antivirus exclusions.
- Use Automatic Deployment Rules (ADR) to download and install updated Defender antivirus definition files, now called "security intelligence updates".
You can also use Intune to manage the Defender antivirus settings on workstations.
- You can find the antivirus policies under Manage in the Endpoint security node of the Microsoft Endpoint Manager admin center.
- Antivirus policies include the same settings as endpoint protection or device restriction profiles for device configuration policy and are similar to settings from device compliance policy. However, those policy types include additional categories of settings that are unrelated to Antivirus. The additional settings can complicate the task of configuring antivirus.
- Policies contain the same type of settings that we can configure using SCCM.
- Policies are assigned to device groups.
How do I onboard devices to Defender for Endpoint?
Onboarding a client to Microsoft Defender for Endpoint will enable Endpoint Detection and Response, Threat and Vulnerability Management and many other SecOps related functionalities. Once onboarded, the endpoint will appear in the Microsoft 365 Defender portal and advanced security events and insights will become available.
There is a straightforward Microsoft Defender for Endpoint onboarding experience, for any client supported by Microsoft Endpoint Manager, whether it is SCCM, Intune, or co-managed.
For SCCM, we will need an onboarding XML file. This is generated in the M365 Defender portal.
- Navigate to Settings > Endpoints > Device management > Onboarding.
- Choose your operating system and deployment method and generate a download package.
- In SCCM, navigate to Asset and Compliance > Endpoint Protection > Microsoft Defender ATP Policies and create a new policy.
- Choose an Onboarding policy and navigate to the configuration file.
- Deploy to a collection of devices.
The configuration is more integrated for Intune. The first step you take is to set up the service-to-service connection between Intune and Microsoft Defender for Endpoint.
- Set up requires administrative access to both the Microsoft Defender Security Center, and to Intune.
- In the MEM portal, select Endpoint security > Microsoft Defender for Endpoint, and then select Open the Microsoft Defender Security Center.
- In Microsoft Defender Security Center, select Settings > Advanced features.
- For Microsoft Intune connection, choose On
- Return to Microsoft Defender for Endpoint in the Microsoft Endpoint Manager admin center.
- Under MDM Compliance Policy Settings, set Connect Windows devices to Microsoft Defender for Endpoint to On
- When this configurations are On, applicable devices that you currently manage with Intune, and devices you enroll in the future, are connected to Microsoft Defender for Endpoint for compliance.
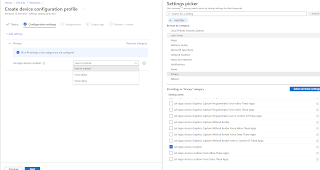
- Finally create an Endpoint Detection and response profile. In the MEM portal, select Endpoint security > Endpoint detection and response.
- Create a policy as shown.
What is Microsoft Defender Security Center app?
This is the UI on the client and can be accessed by clicking on the Defender shield icon on the system tray.
The layout can be customized by using an Endpoint Protection configuration profile in Intune. See where I've blocked the Family Options section.
This is the Microsoft Defender Security Center app without Family Options.
Where does OneDrive fit into all this?
It's a good idea to configure OneDrive in advance for your users by using a GPO.
If you don't you will end up with this warning when Defender is enabled and active. OneDrive is required for file recovery in case of a ransomware attack. The user can continue to set up OneDrive or Dismiss the warning but that's not the best approach.
What advanced features should be configured?
Microsoft Defender has a wide range of options available for configuration using MEM (SCCM or Intune). You should consider configuring all of the following:
Can I customize the Defender Security Center app for my organization?
Yes, you can. You can add details of your organization and support to the Defender Security Center app to assist your end users. Using an Intune Endpoint Protection configuration profile, navigate to the Microsoft Defender Security Center section.
You can enter the organization name and support telephone number, email address and website URL. I've just entered the organization name and website URL here.
This is what it looks like in the Defender Security Center app. You can see a new button on the bottom right.
Click on the button and you'll see the details you have configured.
This configures the registry as shown:Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\Enterprise Customization
What are the high-level steps for a migration?
Microsoft provides good guidance to switch from non-Microsoft endpoint protection to Microsoft Defender for Endpoint.
The high-level steps are as follows (this example uses McAfee):
- Prepare phase
- Get and deploy updates across your organization's devices
- Get Defender for Endpoint.
- Grant access to the Microsoft Defender Security Center.
- Configure device proxy and internet connectivity settings.
- Setup phase
- Reinstall or enable Microsoft Defender Antivirus on your endpoints.
- Configure Defender for Endpoint.
- Add Microsoft Defender for Endpoint to the exclusion list for McAfee.
- Add McAfee to the exclusion list for Microsoft Defender Antivirus.
- Set up your device groups, device collections, and organizational units.
- Configure antimalware policies and real-time protection.
- Phase 3
- Onboard devices to Microsoft Defender for Endpoint.
- Run a detection test.
- Confirm that Microsoft Defender Antivirus is in passive mode.
- Get updates for Microsoft Defender Antivirus.
- Uninstall McAfee.
- Make sure Defender for Endpoint is working correctly.
How do I test Defender functionality?
In the Defender Security Center app we can see at a glance that our policies have been applied.
Also, Microsoft provide assistance to allow us to test demo scenarios. They provide sample files which are harmless and for demonstration purpose only.
You can test cloud-delivered protection.
Network protection
Controlled Folder access
URL reputation
I hope this helps. Until next time.......