Flexible work arrangements and accelerating digital transformation have changed the way we need to secure access. Organizations need an easier, more agile approach to protecting access to all applications and resources. Traditional network security approaches like VPNs don’t scale to these modern demands, they don’t give end users a good experience, and they grant excessive access to the entire corporate network. All it takes is one compromised user account, infected device, or open port for an attacker to access and laterally move anywhere inside your network. Neither identity nor network security controls alone can fully protect all access points. Even if you’ve adopted modern but disjointed access solutions you may leave security gaps that skilled adversaries can exploit. So, you still need to integrate them to address these challenges.
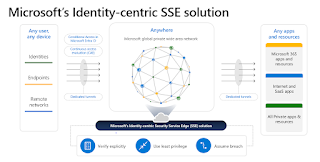
Microsoft's identity-centric Security Service Edge (SSE) solution helps organizations secure access to any app or resource, from anywhere. Conditional Access policies can be enforced that consider identity, device, application, and now network conditions with any application or website.
The Microsoft SSE solution contains two products announced last year, Microsoft Entra Internet Access and Microsoft Entra Private Access.
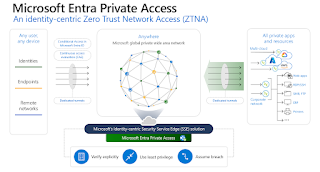
This model is built on Zero Trust principles. It helps to verify each identity and uses risk-based context, giving users access only to applications, resources, and destinations they need to do their job. With Identity and Network Access solutions working together, organizations can bridge the gaps across multiple tools in one place and configure unified identity and network access controls with Conditional Access in Microsoft Entra.
Microsoft Entra Internet Access is an identity-centric Secure Web Gateway (SWG) for SaaS apps and internet traffic that extends Conditional Access policies to protect against malicious internet traffic, unsafe or non-compliant content, and other threats from the open internet. For example, you can block access to all external destinations for your high-risk users or non-compliant devices except limited URLs needed by the user to recover.
I will concentrate on Microsoft Entra Private Access for this blog post. You are probably familiar with Application Proxy in Microsoft Entra, which thousands of organizations use to access private web apps today. Microsoft Entra Private Access is an even better solution and is currently in Preview. It is a complete, identity-centric Zero Trust Network Access (ZTNA) solution that shares the same application connectors but offers so much more, to help organizations simplify and secure access to any private resource, port, or protocol.
For the Entra Private Access blog post we'll concentrate on the following high level steps. Try it in your lab.
- Prerequisites
- Enable Global Secure Access
- Enable Traffic Forwarding
- Install the Connector
- Create Connector group
- Create and publish a private application
- Assign user/group to private application
- Install the Global Secure Access client
- Test and verify private access
- Logs
- Mobile devices
- Conditional Access
Prerequisites
Ok, as always there are some prerequisites to get this working.
- Admin user with one of the following roles: Global Secure Access Administrator, Application Administrator, Security Administrator
- Server to install connector (essentially the application proxy, you'll need local admin rights)
- A server with RDP enabled plus a fileshare
- Test user with Entra ID P1 license (M365 E3 does the trick 😀😀) (see note below *)
- Test client:
- Windows 10/11 64-bit
- Entra ID or hybrid joined
- Internet connection with no LAN or VPN connection to the private application
- Ability to install the Global Secure Access agent (via Intune or local admin)
Enable Global Secure Access
The first step is enable Global Secure access for the tenant.
Global Secure Access is now enabled and you can click Get Started to review the documentation for the next steps.
Enable Traffic Forwarding
Traffic forwarding enables you to configure the type of network traffic to tunnel through the Microsoft Entra Private Access service. You set up profiles to manage how specific types of traffic are managed. Private access traffic can be forwarded to the service by connecting through the Global Secure Access desktop client.
Navigate to Global Secure Access (Preview) > Connect > Traffic Forwarding
Create Connector group
Connector groups are used to assign specific connectors to applications. They give you more control and let you optimize your deployments.
Click New Connector Group > enter a name and associate with the connector.
Create and publish a private application
Now for the services, I want to add a private application for RDP (3389) to a specific server (192.168.10.19). I'll also add access to a fileshare (445) on the same server. Remember we could only use application proxy for web apps before.
Navigate to Global Secure Access (Preview) > Applications > Enterprise Applications
The application is ready to be assigned.
You can also use port 445 to give private access to a fileshare.
Assign user/group to private application
Now we need to assign the enterprise application to a user or group. Navigate to Global Secure Access (Preview) > Applications > Enterprise Applications
Click Add user/group and select who needs to access the application.
Install the Global Secure Access client
Navigate to Global Secure Access (Preview) > Connect > Client Download
The client is available for Windows, Android, iOS and macOS. In this case we want Windows. Download and install the client on the test device. You can automate the installation to managed devices using Intune.
Have a look at the properties.
Test and verify private access
Now let's see if the solution works.
However RDP is working, happy days.
I can also get to the fileshare over port 445.
Logs
Now let's look at the logs to prove it. Navigate to Global Secure Access (Preview) > Monitor > Traffic logs
Clicking on one of the logs brings up the activity details. You can see source and destination IP addresses and destination port, verifying that the connection was made over the internet.
Let's try another test and turn off the proxy.
We can see that the connector is not available........
......and neither is RDP. That is expected behaviour.
Mobile devices
Can we use Entra Private Access on mobile devices?
Sure we can. The Global Secure Access client is built in to Microsoft Defender for iOS and Android so it's very straightforward.
In the Entra Admin Center, navigate to Global Secure Access (Preview) > Global settings > Session management/Adaptive access. Select the toggle to Enable Global Secure Access signaling in Conditional Access.
































No comments:
Post a Comment