Back to Endpoint Protection menu
Back to ConfigMgr 2012 menu
We previously installed the SCEP 2012 client on the devices in our test collection. Now we must ensure that the definition files remain up-to-date on these clients. We do this by integration with the software updates component of ConfigMgr.
We have already configured the Software Update Point to deliver Windows and Office software updates to our endpoints. We will now extend this functionality.
Navigate to Administration > Site Configuration > Sites.
Select your Site and click "Configure Site Components" on the ribbon above. Choose Software Update Point.
Navigate to the Classifications tab.
Choose Definition Updates.
Navigate to the Products tab and choose Forefront Endpoint Protection 2010 (the catalog has not yet been updated to be called SCEP 2012). Click Apply and OK to complete the configuration.
Now manually synchronise with the Microsoft catalog to download the latest definition files. Navigate to Software Library > Software Updates > All Software Updates.
Right click and choose "Synchronise Software Updates". Monitor the download using wsyncmgr.log.
See FEP 2010 chosen and sync starting.
See Definition updates being synchronised and process completing.
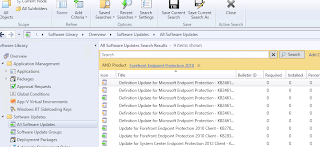
See Definition Updates now available in the console (filter by FEP 2012).
We will now create an Automatic Deployment Rule so that the definition updates can be downloaded and deployed automatically. We don't want to have to do this manually each week.
Navigate to Software Library > Software Updates > Automatic Deployment Rules
Right click and choose to "Create Automatic Deployment Rule"
The Create Automatic Deployment Rule Wizard starts. Enter a Name for the rule and then choose a collection (I have used my test collection). Leave the default "Add to an existing Software Update Group".
Make sure that the "Enable the deployment after the rule is on" is checked. Click Next to continue.
Choose defaults and click Next to continue.
Add Property Filters - Product and Update Classification. Choose FEP 2010 and "Definition Updates or Updates". Click Next to continue.
Choose to run the rule after any SUP sync. Click Next to continue.
Choose "As soon as possible" as the deadline. We want the definition updates to be applied immediately. Click Next to continue.
Click Next.
Click Next.
Click Next.
Choose to create a new deployment package. The source folder must exist and be empty. Click Next to continue.
Choose DP and click Next.
Click Next.
Choose your language and click Next.
Review the summary and click Next to create the ADR.
The ADR has been created. Click Close to exit the wizard.
Note the User Experience configuration for the ADR - I want to see what's going on in my test.
The ADR is configured to run automatically after each scheduled synchronisation but let's run it now for the sake of testing. Right click the rule and choose "Run Now".
Click OK to the pop-up message and the rule is now running.
Monitor progress using the ruleengine.log file. See the rule starting.
See deployment package folder being populated.
Content being downloaded.
Software Update Group does not exist so the rule creates it.
See the Software Update Group.
and the contents of the SUG.
Navigate to Monitoring > Deployments
Look at the progress of the ADR.
Our test client has received the deployment.
Verify the "before and after" definition files on the client.
Saturday, 31 August 2013
Config Mgr 2012 Endpoint Protection: Alerts and subscriptions
Back to Endpoint Protection menu
Back to ConfigMgr 2012 menu
You can configure Endpoint Protection alerts in ConfigMgr 2012 to notify administrators when specific security events occur in your hierarchy. Notifications display in the Endpoint Protection dashboard in the Configuration Manager console, in reports, and you can configure them to be emailed to specified recipients.
You configure alerts in the properties of collections. Navigate to the properties of your collection and open the Alerts tab.
Check the box "View this collection in the Endpoint Protection dashboard". Click Add to add some collection alerts.
Choose the options you need and click OK to continue.
Note that the Conditions box is now populated. Select them in turn and review the options. Configure the Alert Name and Severity as you wish.
When you have configured your options click Apply and OK to finish.
Navigate to Monitoring > Alerts > All Alerts and review the Alerts you have created.
Navigate to Monitoring > Alerts > Subscriptions.
Right click and choose "Configure Email Notification".
Check the box "Enable email notification for alerts" and enter the details of your SMTP server. You should configure your SMTP server to accept anonymous requests for SMTP relay from the ConfigMgr server.
Enter a Sender address (this is irrelevant but should make sense) and click the "Test SMTP Server" button (enter your email address). See successful test above.
See successful test email notification.
Right click Subscription again and this time choose "Create subscription".
Enter a Subscription Name and choose one or more alerts. Enter the System Administrators Distribution List email address (you can enter multiple email addresses if you wish).
See the configured subscription. If the condition you configured is reached the subscription will cause an email to be sent to the Admins with details of the alert.
Back to ConfigMgr 2012 menu
You can configure Endpoint Protection alerts in ConfigMgr 2012 to notify administrators when specific security events occur in your hierarchy. Notifications display in the Endpoint Protection dashboard in the Configuration Manager console, in reports, and you can configure them to be emailed to specified recipients.
You configure alerts in the properties of collections. Navigate to the properties of your collection and open the Alerts tab.
Check the box "View this collection in the Endpoint Protection dashboard". Click Add to add some collection alerts.
Choose the options you need and click OK to continue.
Note that the Conditions box is now populated. Select them in turn and review the options. Configure the Alert Name and Severity as you wish.
When you have configured your options click Apply and OK to finish.
Navigate to Monitoring > Alerts > All Alerts and review the Alerts you have created.
Navigate to Monitoring > Alerts > Subscriptions.
Right click and choose "Configure Email Notification".
Check the box "Enable email notification for alerts" and enter the details of your SMTP server. You should configure your SMTP server to accept anonymous requests for SMTP relay from the ConfigMgr server.
Enter a Sender address (this is irrelevant but should make sense) and click the "Test SMTP Server" button (enter your email address). See successful test above.
See successful test email notification.
Right click Subscription again and this time choose "Create subscription".
Enter a Subscription Name and choose one or more alerts. Enter the System Administrators Distribution List email address (you can enter multiple email addresses if you wish).
See the configured subscription. If the condition you configured is reached the subscription will cause an email to be sent to the Admins with details of the alert.
Config Mgr 2012 Endpoint Protection: Enable SCEP on clients
Back to Endpoint Protection menu
Back to ConfigMgr 2012 menu
Previously we added our Endpoint Protection Point and created our own custom Antimalware Policy. We then deployed this policy to a test collection.
However none of this is of any use if we do not enable Endpoint Protection on clients.
Navigate to Administration > Site Configuration > Client Settings. As before we do not want to interfere the with Default Client Settings so we will create a Custom Client Device Settings.
Right click and choose "Create Custom Client Device Settings".
Enter a suitable name, select "Endpoint Protection" and click OK.
You receive a pop-up with client reboot information. Click OK to acknowledge.
Right click and choose Properties.
Select Yes to "Manage Endpoint Protection client on client computers"
Select Yes to "Install Endpoint Protection client on client computers".
Click OK to Save.
Now right click and deploy to
your test collection.
SCEP client will now be installed on all computers in the test collection when they retrieve their machine policy. They will be defined by our custom antimalware policy.
You can monitor the progress of the SCEP client installation using the EndpointProtectionAgent.log file.
Endpoint has been triggered.
SCEPInstall.exe starts. See the policy file used.
A SCEP icon will appear in the system tray. It is minimised but will open if you click on it.
You can see the application installing if you wish.
EP client is successfully installed.
SCEP 2012 icon now available.
New processes running.
New service.
New registry settings.
SCEP now completely installed on client. Let's review the settings that have been configured by policy.
Virus and spyware definitions are shown as up to date.
Quarantined items.
Settings - note they are all greyed out as there are defined by policy. Let's review the individual settings.
Scheduled Scans.
Default Actions.
Real-time protection.
Excluded files and locations.
Excluded file types.
Excluded processes.
Advanced.
MAPS.
Navigate to Monitoring > Endpoint Protection Status > System Center 2012 Endpoint Protection
Choose a collection and see the client count starting to rise.
Right click a client and see the possible console actions.
Back to ConfigMgr 2012 menu
Previously we added our Endpoint Protection Point and created our own custom Antimalware Policy. We then deployed this policy to a test collection.
However none of this is of any use if we do not enable Endpoint Protection on clients.
Navigate to Administration > Site Configuration > Client Settings. As before we do not want to interfere the with Default Client Settings so we will create a Custom Client Device Settings.
Right click and choose "Create Custom Client Device Settings".
Enter a suitable name, select "Endpoint Protection" and click OK.
You receive a pop-up with client reboot information. Click OK to acknowledge.
Right click and choose Properties.
Select Yes to "Manage Endpoint Protection client on client computers"
Select Yes to "Install Endpoint Protection client on client computers".
Click OK to Save.
SCEP client will now be installed on all computers in the test collection when they retrieve their machine policy. They will be defined by our custom antimalware policy.
Endpoint has been triggered.
SCEPInstall.exe starts. See the policy file used.
A SCEP icon will appear in the system tray. It is minimised but will open if you click on it.
You can see the application installing if you wish.
SCEP 2012 icon now available.
New processes running.
New registry settings.
Virus and spyware definitions are shown as up to date.
Quarantined items.
Settings - note they are all greyed out as there are defined by policy. Let's review the individual settings.
Scheduled Scans.
Default Actions.
Real-time protection.
Excluded files and locations.
Excluded file types.
Excluded processes.
Advanced.
MAPS.
Navigate to Monitoring > Endpoint Protection Status > System Center 2012 Endpoint Protection
Choose a collection and see the client count starting to rise.
Subscribe to:
Comments (Atom)